IC Integrity of Edge-Computing Processors – Meeting the Demands of AI
By: Rob van Blommestein
If you ask most people, they would say that we’re living in an age of artificial intelligence (AI). But the reality is that we’re just getting started. The age of artificial intelligence is still in its infancy.

If you ask most people, they would say that we’re living in an age of artificial intelligence (AI). But the reality is that we’re just getting started. The age of artificial intelligence is still in its infancy. So many of aspects of our lives involve technology but we’re still having to feed that technology or manually operate that technology in order get the results we want. Autonomous driving, IoT, and modern manufacturing all use AI to some extent, but the amount is still very small. Dependence on AI will continue to grow exponentially over the next few years, but in order for applications to meet the demands for more AI, the processors that drive them must evolve. These processors need to be able carry out crucial initial calculations and analyze massive amounts of data quickly and accurately. Being powerful isn’t enough. If AI is to become truly useful, the processors must also be reliable, robust, and trustworthy.
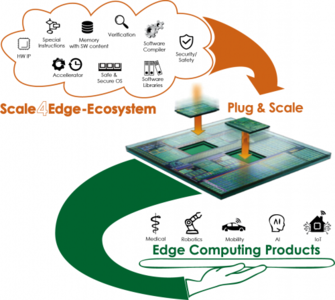
This is where the Scalable Infrastructure for Edge Computing (Scale4Edge) project comes in. This project is funded by the Federal Ministry of Education and Research of the German government under the ZuSE program. The ZuSE projects are intended to meet the urgent prevailing needs and future needs of AI user industries for high-performing, high integrity processors. In that effort, the specific Scale4Edge project is researching and working to create an ecosystem made up of development tools, IP blocks, accelerators, firmware, etc. to significantly reduce development time and costs for application-specific edge processors. The ecosystem will utilize the RISC-V instruction set architecture (ISA) for its scalability, flexibility, and cost-effective attributes. This, in turn, will give edge component providers a competitive advantage and allow them to develop high-quality edge devices quickly.
OneSpin is honored to be part of this illustrious project and is working with a number of partners to assure the integrity of the RISC-V cores for the rapidly growing AI and industry 4.0 markets. Nothing will be left to chance as we’ll provide the verification solutions to exhaustively verify that the cores function as intended, are safe, trusted and secure. In the end, OneSpin’s solutions will be integrated into the Scale4Edge ecosystem.
The computing hardware being built must trusted and secure meaning they are free of any weaknesses or vulnerabilities subject to nefarious attacks. These malicious actions can lead to dangerous consequences and interception of confidential information. Simulation-only verification even if augmented by assertion checking is not enough and can lead to critical bug escapes. Methods for detecting threatening bugs is usually left until the latter stages of design when a fix is much more expensive and time-consuming. The result is a significant impact to the product launch schedule. Furthermore, malicious hardware Trojans are usually not found by simulation-based verification approaches, because they are deliberately designed to hide themselves.
Take for example side channels like Spectre or Meltdown. These exploited vulnerabilities in common processor architectures. They allowed one program/app of a computer/mobile phone to steal the secrets of another program. The fact that it took several tens of years to discover Spectre and Meltdown shows that they are not trivial and that the existing verification technology was not enough to find them. Even worse, after the discovery of Spectre and Meltdown, several other similar side channels were found, but each discovery required a lot of theoretic work.
Technical University of Kaiserslautern (TUK) has been working with researchers at Stanford University to develop a computing method called “Unique Program Execution Checking” (UPEC) that identifies dangerous points of attack in the hardware of open-source processors. TUK will use OneSpin’s 360 Design Verification solutions including the unique GapFreeVerification™ technology to mature the UPEC methodology. For commercial application, OneSpin will integrate UPEC into our Processor Integrity Solution which will be used to prove every aspect of processor behavior and quickly identify all functional errors or malicious code that may be used for spying or sabotage.
When it comes to safety, smart application-specific sensor systems will be developed on the base of RISC-V. The industrial Scale4Edge partners will help to define the requirements and support the research and commercial partners in this effort. ASIC design flows will be optimized from the system-level down to the layout and partners will develop and verify a RISC-V based virtual prototype as well as develop an automotive sensor ASIC prototype. To ensure the safety of these devices, OneSpin will conduct the automated functional safety analysis necessary.
OneSpin is also working with partner, MINRES Technologies on verifying that functional behavior is correct. MINRES creates virtual prototypes (VPs) and supports customers in the deployment of the VPs in the design of embedded software to enable parallelization of hardware and software development. The company develops a generator to produce ISO 26262 conformant RISC-V RTL IP. VP models of its cores will be created as well as other components in the Scale4Edge ecosystem. Formal methods will be integrated for system validation. The use of formal verification in the development of virtual prototypes will lead to increased use of the VPs in the development of security-sensitive applications. The OneSpin Processor Integrity Solution will be used to check the generated RTL with respect to functional correctness, security, and safety.
As you can tell, the Scale4Edge project is of vital importance to the increasing adoption of AI and automation. The work being done will allow processors to grow with the demands of the market in a way that is fast and cost-effective. We’re proud to be able to help assure that these edge-computing processors work as intended and are safe, trusted and secure.